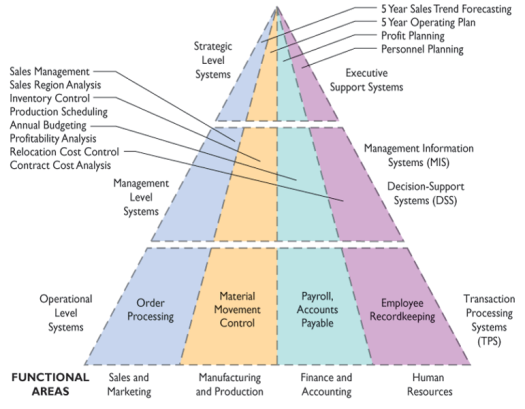
Definition of Information system
An information system is a set of people; procedures and resources that collect transform and disseminates information into an organization.
A Business Perspective on Information Systems
Using feedback completes the information-processing loop. To be a good Information Systems manager, however, you must bring into that loop far more than just the computer data. For instance, your information system reports that you produced 100,000 widgets last week with a “throwback” rate of 10%. The feedback loop tells you that the throwback rate has fallen 2% in the last month. By putting that information into a broader context you will establish that it will cost the organization a huge sum of money because each percentage point on the throwback rate averages $10,000. And when you bring in available external environmental information, your company is 5% above the industry norm. Now that’s information you can use to your advantage.
If you, as a manager, can then take other information from the internal and external environments to come up with a solution to this problem, you can consider yourself “information literate.”
Porter’s value chain is a framework for thinking strategically about the activities involved in any business and assessing their relative cost and role in differentiation. Value can be created by differentiation along every step of the value chain, through activities resulting in products and services that lower buyers’ costs or raise buyers’ performance. The sources of value creation come from policy choices, linkages, timing, location, sharing of activities among business units, integration, learning and institutional factors.
Value chain is the viewing of a business firm as a series of basic activities that add value to the firm’s products or services. The concept of the value chain can be used to identify opportunities to use strategic impact systems. The value chain views the firm as a chain of basic activities that add value to a firm’s products or services. These activities can be categorized as either primary activities or support activities.
Primary activities include inbound logistics, operations, outbound logistics, sales and marketing, and service.
The service activity involves maintenance and repair of the firm’s goods and services. Support activities make the delivery of the primary activities possible and consist of administration and management, human resources, technology, and procurement.
An information system could provide strategic impact if it helped the firm perform its value activities at a lower cost than competitors or if it provided the firm’s customer with added value or service.
Systems to Focus on Market Niche
Nowadays multiple firms are competing for the same market. In order succeed you must identify a specific focal points for a product or service. The firm can serve this narrow target area better than competitors and attract a specific buyer group more easily.
A company can use information systems to “mine” existing information as a resource to increase profitability and market penetration. Firms can use this information to identify and target products for a particular market or product niche, or they may use it to determine ways to serve specific market segments more effectively.
Industry-Level Strategy and Information Systems: Competitive Forces and Network Economics
Look at the relationship between America OnLine and Microsoft. On one hand, they are fierce competitors, going head to head in attracting Web users to their respective Web sites. On the other hand, they work together to supply Web users with desktop icons for accessing the Web.
Information Partnerships
Many times it is more productive and cheaper to share information with other companies than to create it yourself. Information partnerships between companies, even competitors, can enhance a company’s products by aligning them with an industry-wide standard. Vehicle tire manufacturers form information partnerships to share information about standard widths and sizes of tires
Other companies form information partnerships to add extra elements to their products which they could not offer on their own. Lots of companies offer credit cards with their logo and company information. They then share customer information with the credit card companies. Both companies win because they can offer extra services and products not available if they had to act alone.
The Competitive Forces Model.
1. Threat of new entrants into its market
The upstarts can give you fits when you least expect it
2. Pressure from substitute products or services.
Even if they aren’t better than your product, substitutes may be cheaper and customers will be enticed by the lower price.
3. Bargaining power of customers.
The Internet offers customers a unique opportunity to quickly and easily compare prices.
4. Bargaining power of suppliers.
New technology offers suppliers the chance to integrate information systems that tie them closer to their customers
Examples:
- Implementing an enterprise wide Manufacturing Application will help optimize production capacity, from raw materials through final product — regardless of manufacturing methodology. Businesses can automate customer orders, optimize subcontracting, and manage for cost, quality, and compliance.
- Implementing a Financial System will meet the growing demands of global financial reporting and tax requirements with one accounting, tax, banking and payments model.It will also enable shared services across businesses and regions.
- The implementation of Performance Management Applications will support a broad range of strategic and financial performance management processes and enable management excellence. It will drive profitable growth for a company by delivering predictable results, improving transparency and compliance, and increasing business alignment.
- The implementation of Business Intelligence Applications will deliver intuitive, role-based intelligence for everyone in the organization which will enable better decisions, actions and business processes and deliver value from multiple data sources.
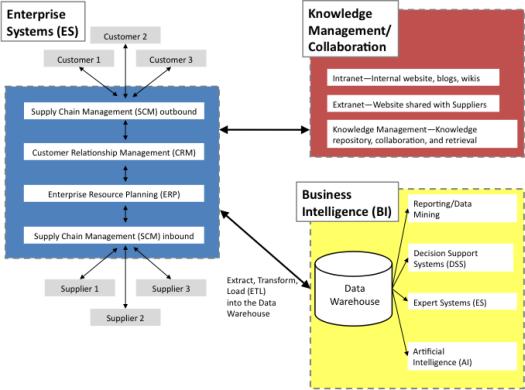
IS Systems in Business
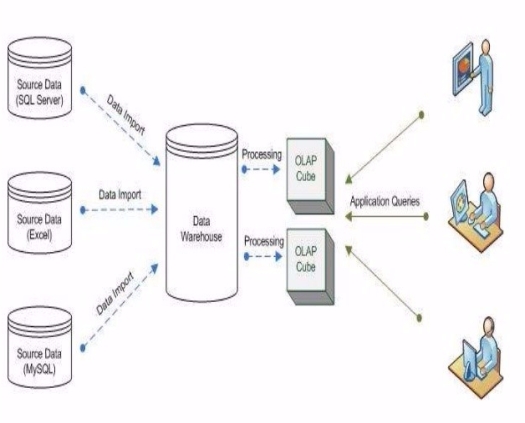
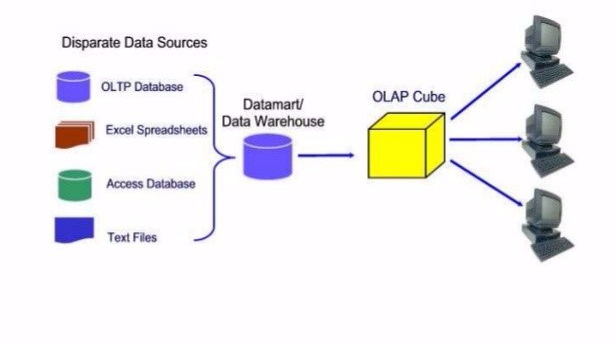
Role of IS in business information value chain